Distributed Denial-of-Service (DDoS) attacks are not a new concept, but they have proven to be an effective way of devastating targeted companies. As the name implies, DDoS is an attempt to deny a service to legitimate users by overwhelming the target with activity. The Gaming, Media, and IT services industry are typically targets for such attacks, but that is not to say that Government or Financial are not within the scope.
What Is a Denial of Service Attack?
A DoS attack is an attempt to make a system or server unavailable for legitimate users and, finally, to take the service down. This is achieved by flooding the server’s request queue with fake requests. After this, server will not be able to handle the requests of legitimate users.
In general, there are two forms of the DOS attack. The first form is on that can crash a server. The second form of DoS attack only floods a service.
Distributed Denial of Service Attack – DDoS:
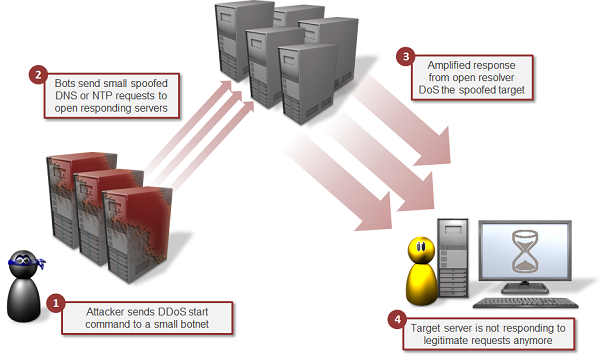 This is the complicated but powerful version of DoS attack in which many attacking systems are involved. In DDoS attacks, many computers start performing DoS attacks on the same target server. As the DoS attack is distributed over large group of computers, it is known as a distributed denial of service attack.
This is the complicated but powerful version of DoS attack in which many attacking systems are involved. In DDoS attacks, many computers start performing DoS attacks on the same target server. As the DoS attack is distributed over large group of computers, it is known as a distributed denial of service attack.
To perform a DDoS attack, attackers use a zombie network, which is a group of infected computers on which the attacker has silently installed the DoS attacking tool. Whenever he wants to perform DDoS, he can use all the computers of ZOMBIE network to perform the attack.
In simple words, when a server system is being flooded from fake requests coming from multiple sources (potentially hundreds of thousands), it is known as a DDoS attack. In this case, blocking a single or few IP address does not work. The more members in the zombie network, more powerful the attack it. For creating the zombie network, hackers generally use a Trojan.
Where are These Attacks Coming From?
Where these attacks come from and who is being attacked can vary depending on what is going on in the world, but primarily there are a handful of top counties that always seem to be tint he mix of thing of DDoS attacks.
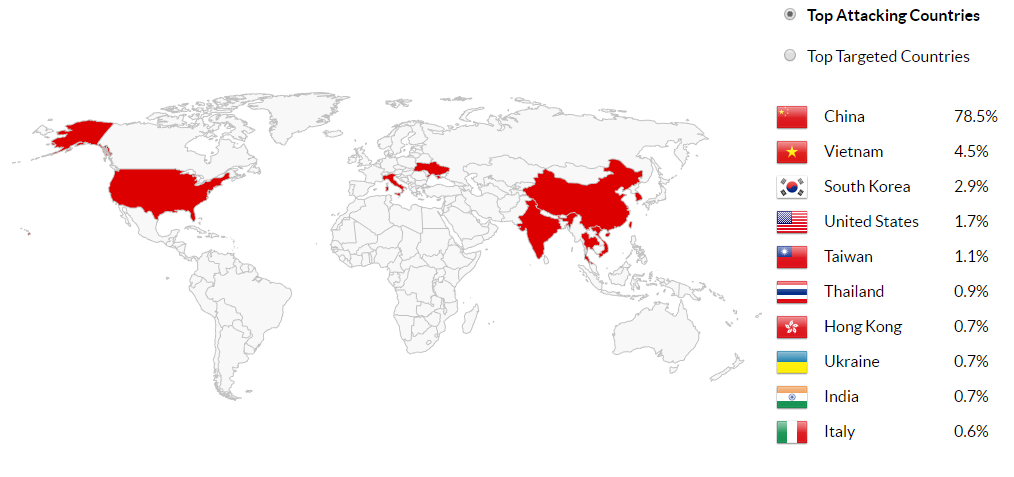
In Q4 2017 Imperva recorded the top Attacking countries.
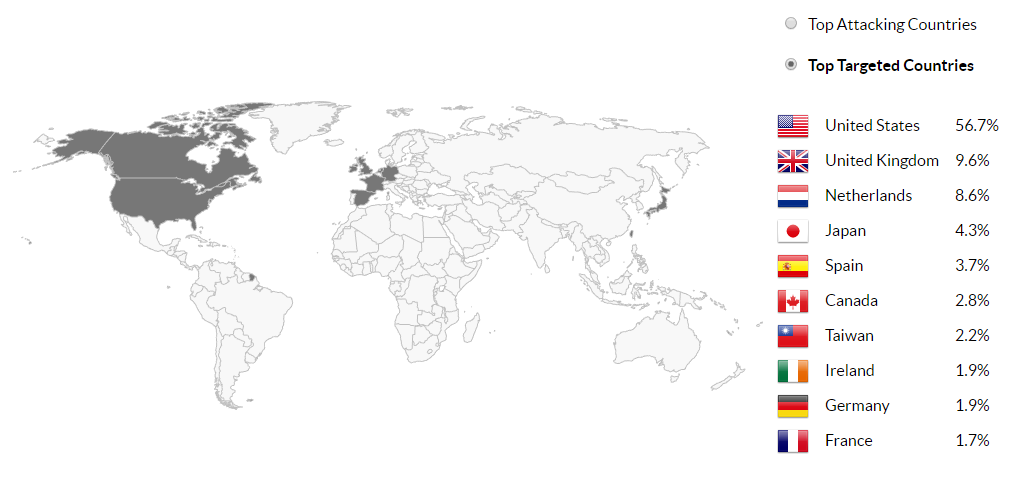
In Q4 2017 Imperva recorded the top Attacked countries.
Real Time DDoS Tracking Tools:
Digital Attack Map is a live data visualization of DDoS attacks from around the globe, built through a collaboration between Google Ideas and Arbor Networks. The tool showcases anonymous attack data to let users see historical and current DDoS attack trends happening at any given day.
Attacks are displayed as dotted lines, scaled to size, and placed according to the source and destination countries of the attack traffic when known. Some features include:
- Use the histogram at the bottom of the map to explore historical data.
- Select a country to view DDoS activity to or from that country.
- Use the color option to view attacks by class, duration, or source/destination port.
- Use the news section to find online reports of attack activity from a specified time.
- View the gallery to explore some examples of days with notable DDoS attacks.
Digital Attack Map stores historical data of DDoS attacks from around the world. You can scroll down and click anywhere within the timeline to get a date analysis of what DDoS attacks that occurred on that day.
Note: In the below real time Digital Tack Map you may need to scroll down to the time line and click to get todays date.
How To Protect From DDOS Attacks?
Truth be told there is no real way to Prevent a DDoS attack. If your website is openly accessible to the World Wide Web then you have the potential to get hit by a DDoS attack.
 To protect your website, you need to be able to block or absorb malicious traffic. Webmasters can talk to their hosting provider about DDoS attack protection. They can also route incoming traffic through a reputable third-party service that provides distributed caching to help filter out malicious traffic — reducing the strain on existing web servers. Most such services require a paid subscription, but often cost less than scaling up your own server capacity to deal with a DDoS attack.
To protect your website, you need to be able to block or absorb malicious traffic. Webmasters can talk to their hosting provider about DDoS attack protection. They can also route incoming traffic through a reputable third-party service that provides distributed caching to help filter out malicious traffic — reducing the strain on existing web servers. Most such services require a paid subscription, but often cost less than scaling up your own server capacity to deal with a DDoS attack.
Mitigation
Mitigating the impact of a DDoS attack is not easy, but there are a few best practices that can help reduce the damage.
- Have an incident response plan ready and know who to call.
- Verify server configuration and protect your server.
- Use a layered filtering approach and partner with external service providers.
- Build scalability and flexibility into your environment.
- Know your normal network behavior.
Acmetek Global Solutions Inc. the SSL Support Desk’s parent website features DDOS solutions through Imperva from a pretty impressive service called Incapsula.
Other Real Time DDOS Detections Tools:
There are many free real time tools out there without the need for a download to see what DDOS attacks are going live. Featured here the Fortinet – ForceGuard and Kaspersky’s Cybermap.





