 Cisco Wireless Lan Controller (WLC) is a very complex system with unconventional implementation of its keypairs for encryption. CSR creation and certificate installation may vary as your custom environment system may differ. Below are generalized instructions.
Cisco Wireless Lan Controller (WLC) is a very complex system with unconventional implementation of its keypairs for encryption. CSR creation and certificate installation may vary as your custom environment system may differ. Below are generalized instructions.
The utility “Openssl” is used to generate the key and CSR and used to perform conversions. This utility comes with the Openssl package and is usually installed under /usr/local/ssl/bin. If you have a custom installation, you will need to adjust these instructions appropriately.
To generate a CSR and Install your SSL/TLS certificate after it has been issued on a Cisco WLC perform the following.
Step 1: Generating your private key pair:
- On the Apache system type using Open SSL perform the following command at the prompt.
Note: The files you create will be saved in a director of your choice or by defaultopenssl genrsa -out privatekeyfilename.key 2048
Step 2: Generating your CSR:
- Type the following command at the prompt.
openssl req -new -key privatekeyfilename.key -out csrfilename.csr
- Example:
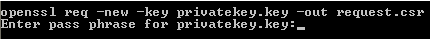
Note: If using openSSL on Windows, you may need to specify the path to openssl.cnf such as the following:openssl req -new -key privatekeyfilename.key -config "c:\Apache Software Foundation\Apache2.2\conf\openssl.cnf" -out csrfilename.csr
- Specify the following information as it applies to your Organization and Website:
- Country Name: Use the two-letter code without punctuation for country, for example: US or CA.
- State or Province: Spell out the state completely; do not abbreviate the state or province name, for example: Massachusetts
- Locality or City: The Locality field is the city or town name, for example: Boston. Do not abbreviate. For example: Saint Louis, not St. Louis
- Company: If the company or department has an &, @, or any other symbol using the shift key in its name, the symbol must be spelled out or omitted, in order to enroll. Example: XY & Z Corporation would be XYZ Corporation or XY and Z Corporation.
- Organizational Unit: The Organizational Unit (OU) field is the name of the department or organization unit making the request. To skip the OU field, press Enter on the keyboard.
- Common Name: The fully-qualified domain name, or URL, you’re securing. for example “www.domain.com.” The Common Name must match DNS Hostname on the Virtual Interface.
- Important Note: You might be prompted to associate a password for your CSR. Leave this blank and press Enter. Associating a password with your CSR will encrypt it and will cause issues with enrollment.
- Note: WLC’s do not like wildcard certificates. Make sure the specify a non-wildcard common name.
A public/private key pair has now been created. The private key is stored locally on the server (remember its location and name as it will be required for Installation).
Your CSR request has been created and is ready for you to copy and paste its contents into the enrollment portal.
Step 3: Downloading your SSL Certificate its Intermediate CA and Root certificate:
For a Complete installation of your Server certificate on your Cisco WLC you will need three things. Your Server Certificate, Its Intermediate CA, and its Root Certificate. You will create a master all-certs.pem file that will need to be converted into a .pfx file with the private key that was created during CSR creation.
- If you had the option of server type during enrollment and selected Other you will receive a x509/.cer/.crt/.pem version of your certificate within the email. Alternately you can access your Certificate User Portal by the supplied link in the email to pick up the x509 version of your certificate.
- On your computer operating system open a standard text document or notepad. For example you can right click on your desktop on windows go New and select Text Document.
- Copy the SSL certificate and make sure to copy the —–BEGIN CERTIFICATE—– and —–END CERTIFICATE—– header and footer Ensure there are no white spaces, extra line breaks or additional characters.
- If your intermediate CA certificate for your product is not in the body of the email you can access your Intermediate CA also in a link within that email typically or contact your CA for Support. Click here to see a list of intermediate and root the SSL SupportDesk has on file.
- Copy and paste the contents of your Intermediate and root certificate into the same Notepad/Text Doc of your Server Certificate. You should have one file that looks like this and saved with what ever name you like with a .pem extension.
Note: Some CAs may give you an Apache intermediate bundle or will require installation of two intermediates . These two intermediates are to be kept together stacked on top of each other and inserted into the example below when making your master all-certs file for installation.
——BEGIN CERTIFICATE——
*Server Device/SSL cert*
——END CERTIFICATE——
——BEGIN CERTIFICATE——
*Intermediate CA cert *
——END CERTIFICATE——–
——BEGIN CERTIFICATE——
*Root CA cert *
——END CERTIFICATE——
Step 4: Combining your Master all-certs.pem file with private .key into .pfx and then back to a .pem:
You now need to combine your Master all-certs.pem file with the private key that you generated back during CSR generation privatekeyfilename.key. into a single .pfx file and then once your all-certs.pem and .key file are merged convert it back into a .pem again…
- Move your two files into the folder where OpenSSL.exe resides keep in mind OpenSSL can be a custom environment. these are generalized instructions you may have to adjust thing appropriately.
(typically C:\Program Files\GnuWin32\OpenSSL\bin\):
• privatekeyfilename.key
• all-certs.pem - Now with those two files int he same directory perform the following Open OpenSSL (via Command Line) and execute the following commands (in one line).
openssl>pkcs12 –export -in all-certs.pem -inkey privatekeyfilename.pem –out all-certs.p12 -clcerts -passin pass:check123 -passout pass:check123
openssl>pkcs12 –in all-certs.p12 –out final-cert.pem -passin pass:check123 –passout pass:check123
Note: In this command, you must enter a password for the parameters –passin and -passout. The password that is configured for the -passout parameter must match the certificate password parameter that is configured on the WLC. In this example, the password that is configured for both the -passin and -passout parameters is check123. You should now have a .pem file that will need to be moved and downloaded into your WLC if it is not there already.
Step 5: Uploading your certificate to the WLC:
- Login to your WLC via the Web GUI, and choose the following path:
Web GUI > Security > Web Auth > Certificate: Check the box: Download SSL Certificate. - In the File Path field, enter the directory path of the certificate.
- In the File Name field, enter the name of the certificate.
- In the Certificate Password field, enter the password that was used to protect the certificate.
- Click Apply.
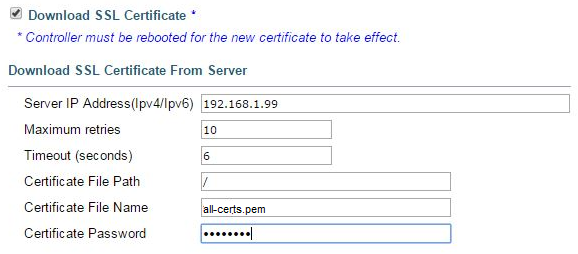
- After the download is complete, choose Commands > Reboot > Reboot.
- If prompted to save your changes, click Save and Reboot.
- Click OK in order to confirm your decision to reboot the controller.
Congrats you have just configured your Cisco WLC with your new server Certificates
If you are unable to use these instructions for your server, Acmetek recommends that you contact either the vendor of your software or the organization that supports it.
Cisco Support:
For Cisco Support on WLC click here



